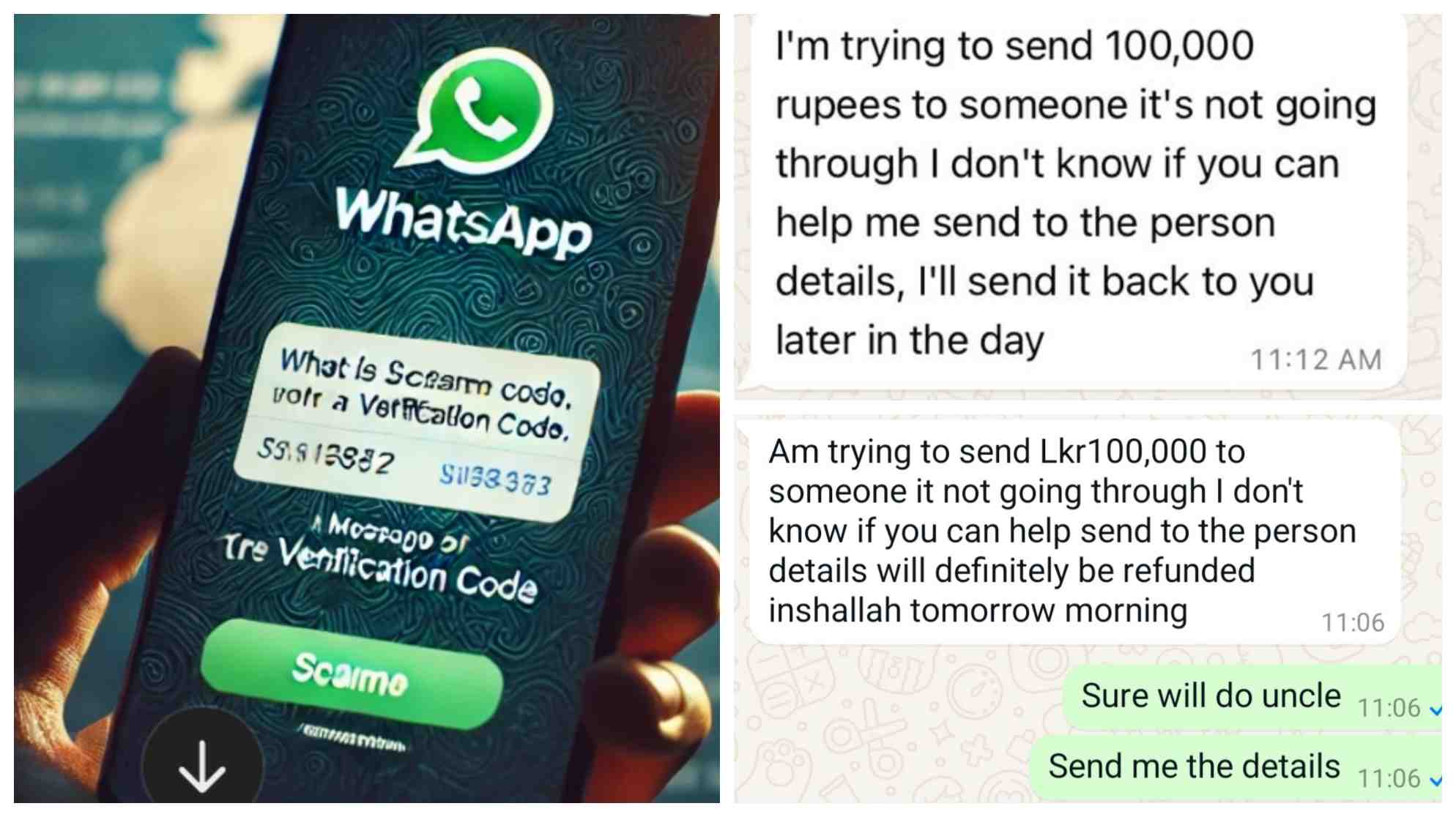
Sri Lanka is experiencing a rise in WhatsApp account hacks, with cybercriminals using verification code manipulation to gain access to accounts and defraud contacts.
In recent incidents, users have reported receiving unexpected WhatsApp verification codes. Scammers then contact users, posing as friends or acquaintances, to request the code, which, once shared, grants hackers control over the account.
A Colombo businessman, who recently fell victim to the scam, described his experience: “I received a message from a friend’s wife, a known contact, who asked how I was doing. After exchanging pleasantries, she mentioned she had sent a code by mistake and needed it back. Assuming it was genuine, I shared the code. My WhatsApp was immediately hacked,” he said. Once his account was compromised, cybercriminals used it to send messages to his contacts, requesting small sums of money under the pretence of financial distress. “A friend even reached out to my wife to check if I was in trouble. Despite reinstalling WhatsApp multiple times, I couldn’t regain access even after 72 hours,” he added. He has since filed a police complaint and reached out to WhatsApp support.
Forensic cybercrime experts explained the two-step approach hackers use: “First, they compromise the user’s WhatsApp account through the verification code, and then target the user’s contacts with requests for financial help.” Victims have reported sending amounts between Rs 50,000 and Rs 100,000, believing they were aiding a friend in need.
A retired officer shared a similar experience. “I got a call from a foreign number requesting me to join a Zoom call for a religious discussion,” he said. “To join the Zoom call, they said they would send a verification code. I sent them the verification code, and soon after, my WhatsApp account was hacked, and they sent messages to my contacts asking for money, pretending to be me. Unfortunately, some of my friends sent money to them,” he said. “The bank account given was under a name in Gampola. I later found out that the account was also compromised.”
Cyber experts caution users to “always be cautious” when a WhatsApp message requests a verification code. “Any OTP or code received should never be shared,” they said.
Victims are advised to alert their contacts via social media if their accounts are hacked, helping prevent further scams. With the increasing prevalence of this scam, Sri Lankan authorities are encouraging users to enable two-step verification on their accounts and to remain vigilant when receiving any messages involving verification codes. (Newswire)
Here are the most common ways hackers attempt to steal data, launch scams and ransomware, or spread malware on WhatsApp.
- Social Engineering – WhatsApp number hack
Social engineering is a method of manipulating people to extract sensitive information, such as passwords or verification codes. In the context of WhatsApp, hackers can register your number on their device and request a verification code to access your account.
How it works. Hackers register your number on the WhatsApp application by downloading the app to their phone, entering your telephone number, and getting the verification code to access the account. The verification code is sent to your phone, and then the hacker will try to trick you into handing over the code.
How to protect yourself. If you receive a text message with a WhatsApp verification code and one of your WhatsApp contacts immediately contacts you, asking you to share the verification code, don’t give it. Because once you do it, the hacker can use it to access your WhatsApp account.
- WhatsApp Forward Call
“WhatsApp Forward Call” is a method hackers use to gain access to a victim’s account and all incoming calls.
How it works: You may receive a message, email, or phone call that tricks you into dialing a number with a Man Machine Interface (MMI) code. If you fall for the trick and make the call, your calls will automatically be forwarded to the attacker’s number. After the attacker has forwarded your calls to their phone, they can install WhatsApp, register your number, and request a verification code by phone call.
How to protect yourself. Avoid responding to messages or requests from unknown contacts. Also, avoid calling unknown numbers.
- WhatsApp Web hacking
Another popular method is hacking WhatsApp’s web version. To access and log in to WhatsApp Web, users have to scan a QR code that appears on the web browser service.
How it works. Hackers take the QR code from WhatsApp Web and place it on a malicious page. If you scan that fake QR code using WhatsApp — or sometimes even with your phone camera, they can steal your login credentials and use them to hack your account.
How to protect yourself. Before scanning, check any QR code before scanning it. You can use Bitdefender Scamio to confirm whether a QR code is genuine.
- WhatsApp Spyware
Hackers can use spyware to access the victim’s WhatsApp account by installing it on their device.
How it works. The most common ways people unintentionally infect their phones with spyware are through malicious links, third-party apps, and email attachments they click and/or download. Once installed, the spyware can record the victim’s WhatsApp messages and send them to the hacker, who can gain access to messages, audio, statuses, photos, videos, and more.
How to protect yourself. Protect your phone with a mobile security solution that detects and blocks malicious texts, messages, and links, scans webpages and apps, and alerts you in case of danger. Regularly review the permissions of the apps on your phone and check for any suspicious apps you do not remember installing.
- WhatsApp Dark Web attacks
WhatsApp hacking tools and services are sold on the Dark Web, and so are personal information leaked in breaches, phone numbers included.
How it works. Fraudsters get all the information they need from the Dark Web and then get into WhatsApp accounts to get money from you or your family.
How to protect yourself. Check regularly whether your personal information is available online and take steps to minimize your digital footprint. Consider using a digital identity monitoring tool like Bitdefender Digital Identity Protection which can alert you in real-time when your personal information is on the public or Dark Web and help you take the necessary measures to reduce risks.
